Silobreaker Update 2021年05月04日
インターネット上でトレンドとなっている脅威アクター、マルウェアのランキングです。
Silobreaker の API を使用して作成しています。このページに関する説明はこちらをご覧ください。
Threat Actor
| Name | Move | Volume 1d | Volume 7d | Volume 30d |
|---|---|---|---|---|
| Phantom Troupe |  |
3 | 3 | 3 |
| Donot Team | 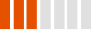 |
3 | 3 | 6 |
| APT40 | 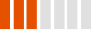 |
2 | 2 | 4 |
| Lab Dookhtegan |  |
3 | 6 | 10 |
| APT30 |  |
5 | 52 | 52 |
Malware
| Name | Move | Volume 1d | Volume 7d | Volume 30d |
|---|---|---|---|---|
| Buer Loader |  |
47 | 47 | 47 |
| Pay2Key Ransomware | 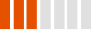 |
9 | 13 | 14 |
| Start Ransomware | 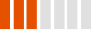 |
3 | 3 | 6 |
| Chopper ASPX Web Shell |  |
4 | 11 | 15 |
| RoyalRoad |  |
4 | 17 | 20 |
Related documents
- ThreatActor:Phantom Troupe
- TurgenSec finds 345,000 files from Filipino solicitor-general’s office were breached
- Published by Zephyrnet.com (2021-05-03 12:25:00)
- Entities:
- Company:TurgenSec Ltd, Keyphrase:Breach, Organization:Government of the Philippines, Country:Philippines, ThreatActor:Phantom Troupe
- ThreatActor:Donot Team
- JAMESWT_MHT – Mentioned
#RTF #APT sample which belongs to APT-C-35 group
https://t.co/CddAnRIPiJ - Published by JAMESWT_MHT – Twitter (2021-05-03 23:04:55)
- Entities:
- HashTag:#rtf, ThreatActor:Donot Team, HashTag:#apt, Username:@jameswt_mht, Subdomain:bazaar.abuse.ch
- ThreatActor:APT40
- Group dedicated to exposing Chinese government secrets begins countdown for reveal this week
- Published by Daily Dot (2021-05-04 02:45:55)
- Entities:
- Organization:Intrusion Truth, ThreatActor:APT3, Organization:Government of the People’s Republic of China, Keyphrase:Computer Hacker, ThreatActor:APT10
- ThreatActor:Lab Dookhtegan
- Treadstone71LLC – Source Code for Binder project – Lab Dookhtegan – long before #Flashpoint The Cyber Shafarat – Treadstone 71 https://t.co/xokBHhrrIT
- Published by Treadstone71LLC – Twitter (2021-05-04 03:54:20)
- Entities:
- HashTag:#flashpoint, ThreatActor:Lab Dookhtegan, Company:Treadstone 71, Username:@treadstone71llc, Keyphrase:Source Code
- ThreatActor:APT30
- Naikon APT Group is Now Using Nebulae Backdoor
- Published by Cyware (2021-05-04 05:29:00)
- Entities:
- Malware:Nebulae Backdoor, ThreatActor:APT30, Malware:RainyDay Backdoor, Keyphrase:Cyber Espionage, Keyphrase:Malware
- Malware:Buer Loader
- New Variant of Buer Loader Written in Rust
- Published by Reddit – BlueTeamSec – RSS (2021-05-04 02:16:34)
- Entities:
- Malware:Buer Loader
- Malware:Pay2Key Ransomware
- malwrhunterteam – “N3tw0rm provides enterprise-level of ransomware attacks!”
😂
Either they are trying to fake as Pay2Key as much as p… https://t.co/ghBB2WWp0A - Published by malwrhunterteam – Twitter (2021-05-03 17:45:21)
- Entities:
- Malware:Pay2Key Ransomware, Username:@malwrhunterteam, Keyphrase:Fake, Organization:MalwareHunterTeam, Domain:twitter.com
- Malware:Start Ransomware
- Update to Pulse Connect Vulnerabilities
- Published by ISSSource – RSS (2021-05-04 04:52:28)
- Entities:
- Product:Pulse Connect Secure, Keyphrase:Vulnerability, Company:Ivanti, Keyphrase:Threat Actor, Vulnerability:CVE-2021-22893
- Malware:Chopper ASPX Web Shell
- TrendMicro – #ICYMI: Hacktivism’s reemergence explained, Hello ransomware uses updated China Chopper web shell, the first malici… https://t.co/QK3ApDRGwJ
- Published by TrendMicro – Twitter (2021-05-03 23:48:16)
- Entities:
- Malware:WickrMe Ransomware, Malware:Chopper ASPX Web Shell, HashTag:#deepfakes, Malware:China Chopper, Username:@trendmicro
- Malware:RoyalRoad
- Chinese hackers targeting Russian nuclear submarine design firm with PortDoor malware
- Published by TEISS.co.uk (2021-05-03 16:30:00)
- Entities:
- Keyphrase:Malware, Keyphrase:Nuclear Submarine, Keyphrase:Computer Hacker, ThreatActor:Karma Panda, Keyphrase:Chinese

